چند ماه پیش ویروسی در اندروید منتشر شد که بسیار به کرمهای ایمیلی اوایل سال ۲۰۰۰ شبیه بود. حالا بار دیگر با این پدیده مواجه هستیم. این ویروس به نام «Andr/SlfMite-A» خودش را به عنوان یک لینک پیام کوتاه برای ۲۰ کانتکت مهم گوشی شما میفرستاد و در نهایت اپلیکیشن مخربی را روی سیستم شما نصب میکرد. بار دیگر با نسخه جدید به نام «Andr/SlfMite-B» رو به رو هستیم که خودش را به عنوان یک اپلیکیشن گوگل پلاس جا میزند در حالیکه قطعا چنین نیست و این یک اپلیکیشن تقلبی و دام است. در ادامه با روش مقابله با این ویروس همراه گجت نیوز باشید .
ویروس جدید که در واقع یک کرم دیجیتال است، از روشی مدرن استفاده میکند که در آن از شبکهای مانند یک شبکه باتنت به نام «call home» استفاده میکند و قدمهای بعدی خود را به صورتی متغیر و دینامیک تعیین میکند و برنامهریزی از پیش تعیین شدهای وجود ندارد. (باتنت به مجموعهای از سیستمها گفته میشود که همگی آلوده شدهاند و اختیار آنها بدون اطلاع دارندگان آنها در اختیار یک فرد یا گروه قرار گرفته است).
در کرم جدید به جای ۲۰ کانتکت، پیام به ۵ کانتکت فرستاده میشود و این ممکن است به دلیل احتیاط بیشتر باشد. هم چنین عبارتهایی مانند «Hey, try it» و «Hi buddy» در متن آنها مشاهده شود.
روش مقابله
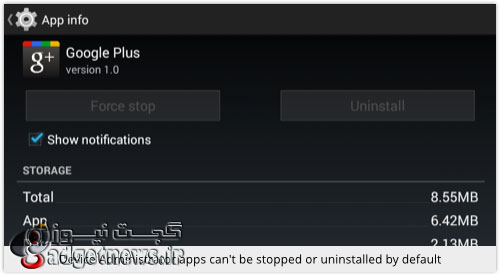
این بدافزار خودش را به عنوان یک برنامه «device administrator» جا میزند و ادعا میکند که ویژگیهای بهبود یافته امنیتی برای قفل صفحه ارائه میکند که در واقع تلاش این بدافزار برای قرار از شناسایی شدن است. اگر به Settings رفته و بخش Apps را انتخاب کنید و روی آیکون گوگل پلاس تقلبی بزنید میبینید که گزینه Uninstall برای این اپلیکیشن خاکستری و غیرفعال است.
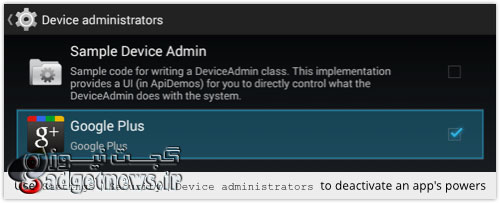
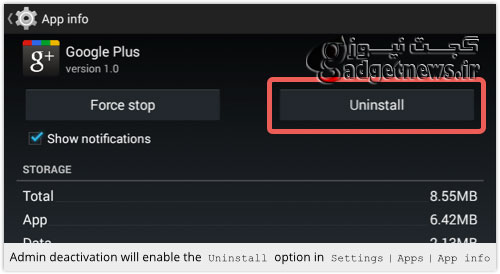
حال باید به آدرس Settings <Security <Device administrator رفته و اختیار داده شده به این اپلیکیشن را غیرفعال کرده و بار دیگر آن را Uninstall کنید.
Back in June 2014, we wrote about an Android virus that worked a bit like the email worms of the early 2000s.
Andr/SlfMite-A sent itself as an SMS link to your top 20 contacts, and then foisted a third party app for an alternative Android software market onto your phone.
Well, it’s made a comeback that we’re detecting as Andr/Slfmite-B.
This variant pretends to be a Google Plus app, though of course it is no such thing:
The modus operandi and the coding structure are similar to the SlfMite-A variant, but it’s both pushier and more flexible than before.
This time, it’s using a botnet-style “call home” to download data to decide what to do next, rather than having its malicious activities pre-programmed.
The downloaded control data is fetched via HTTP and includes settings such as how many SMSes to send; what SMS text to use; where to link to; and more:
SMS sending
When we looked, the SMS_LIMIT was set to 5, rather than the 20 contacts that were targeted by SlfMite-A.
We can’t tell you why its virulence has been reduced since last time, but it may be cybercriminal caution following the recent Andr/SmsSend-FA virus outbreak.
SmsSend-FA was better known as the Heart App, and its aggressive use of SMS (it spread to your first 99 contacts) brought it to the attention of mobile phone operators and law enforcement very rapidly.
The Heart App’s messages were quickly blocklisted and the perpetrator arrested.
There are two possible SlfMite-B SMS messages, using the “Hey, try it” and “Hi buddy” texts in the SMS_TEMPLATE data you see above.
We can’t tell you what the SMS links we saw were supposed to do, because they rely on a URL shortening service (X.CO, run by GoDaddy), and they have been neutralised so that they no longer redirect anywhere:
We’ll assume, given the other similarities with SlfMite-A, that at least one of the SMS links was intended to spread the infection, making this variant a virus (or, more specifically, a worm) just like the old one.
Of course, the crooks could change the SMS_OFFER data and future SMSes sent by the malware will again be dangerous.
So if you see messages like the ones shown above, be sure to delete them and don’t click through, even though they seem to come from your friends.
Self-protection
Another new trick up SlfMite-B’s sleeve is to copy the self-protection behaviour of the FBILock-A malware we wrote about in July, after SlfMite-A came out.
It registers itself as a device administrator, allegedly with the handy (and security-oriented) feature of improving your lock screen safety:
But this step exists only to make the malware harder to remove.
If you head to Settings | Apps and tap on the bogus “Google Plus” icon, you will find the [Uninstall] button is blanked out because of the app’s device administration powers:
To sort this out, first, head to Settings | Security | Device administrators; you can then [Deactivate] the administration privileges of the malware:
Finally, head back to Settings | Apps to dispose of it:
The hard sell
Unlike the email viruses of the early 2000s, many of which existed to cause havoc merely by spreading (though what havoc that was!), SlfMite-B aims to make money.
Amongst the downloaded configuration information is a pair of data items, each of which defines:
A URL from which to download a graphical icon
A name to go with that icon
A URL to visit if the icon is clicked
Once downloaded, the two icons are placed in prime position on your home screen, presumably in the hope that you will click them and generate some affiliate revenue for the crooks.
The icon data that our copy of the malware received during testing pitched two “products” at us:
Clicking on the Mobo Market icon downloaded an app entitled MoboMarket.apk.
This seems to be signed by Mobo Market, a Chinese company that runs an alternative Android marketplace.
Clicking on the Mobogenie icon eventually redirected us to a web page urging us to sign up for a perpetual subscription SMS service (approximate cost $20/month, billed daily) under the guise of free wallpapers:
As if that weren’t enough, the malware also includes code to extract and upload confidential data from your phone, such as your device ID, the phone’s IMEI (International Mobile Equipment Identity, a unique electronic identifier that goes with your handset), and your entire contact list.
What to do
How to remove the fake Google Plus app is described above.
You need to revoke the app’s Device Administration rights in Settings | Security | Device administrators, before heading to Settings | Apps to uninstall it.
If you installed the MoboMarket.apk as well, you probably want to uninstall it, given its association with this malware.
 گجت نیوز آخرین اخبار گجتی و فناوری های روز دنیا
گجت نیوز آخرین اخبار گجتی و فناوری های روز دنیا